From October 22-25, NMFTA hosted its annual Digital Solutions Conference on Cybersecurity in Houston, TX. The presentations contained powerful information for any company in the trucking industry that’s concerned about cybersecurity for its enterprise and/or assets. Of course, that needs to be the entire industry. This is part of a series of blogs that summarize the information presented for those who could not be there.
TOPIC: Available Government Resources
Presenters:
– Ernesto Ballesteros – Cybersecurity State Coordinator, Cybersecurity and Infrastructure Security Agency (CISA)
– Jerrel Conerly – Cybersecurity Advisor, Region 6, Cybersecurity and Infrastructure Security Agency (CISA)
– Takeda Parker-Bradford – Compliance Administrator, Transportation Security Administration (TSA)
– Clarke Skoby – Technical Special Agent, U.S. Secret Service (USSS)
– Mike Alvarez – Network Intrusion Forensic Analyst, U.S. Secret Service (USSS)
– Trina Martin – Cyber Intelligence Analyst, Federal Bureau of Investigation (FBI) Cyber Task Force
The federal government showed up in a significant way at this year’s Digital Solutions Conference on Cybersecurity, and its representatives offered one clear message to the trucking industry: We’re here to help, and we have extensive knowledge that can help keep you safe from cyberattacks.
In a series of presentations, federal agency officials explained the various roles they play in protecting industry from cyberattacks, as well as how any company looking for help can connect with them.
We’ve broken down the information agency-by-agency to make it easier for readers to make use of it.
The Cybersecurity and Infrastructure Security Agency (CISA)
CISA representatives Ernesto Ballesteros and Jerrel Conerly shared information with conference attendees during separate sessions.
They explained that the mission of CISA is to collaborate with the private sector to enhance its resiliency against cybersecurity threats. CISA is not a law enforcement agency, although its experts will sometimes coordinate with federal law enforcement on certain investigations because of their knowledge of the field.
CISA’s role is to help companies by assessing their level of risk, promoting best practices and strategies, helping to build security capacity, educate and raise awareness, listen to stakeholders, and offer support in the event of an incident.
Most of the time, CISA’s contact with a company occurs before there is a breach.
“We provide advice and counsel, and subject matter expertise, at no cost because you’ve already paid for these services as American taxpayers,” Ballesteros said. “We help to identify areas to improve upon, where to make investments or stand-up capabilities. We help folks understand how to put it into play in the real-world setting.”
Some of this support could come in the form of tabletop exercises, in which companies test their security infrastructure by finding out what happens when someone tries to hack in.
Ballesteros and Conerly said ransomware is one of the most common and dangerous threats, and Conerly strongly urged companies not to pay ransom if they are targeted.
“Once you start paying the money, they’re going to come back again two or three years later,” Conerly said. “And they’re going to tell their friends you’re an easy mark.”
Conerly urged trucking companies to focus on four fundamental measures of protection:
- Multi-factor authentication
- Strong passwords
- Recognizing and reporting phishing
- Updating software promptly
Ballesteros also talked at length about business e-mail compromise, in which employees unknowingly let an attacker in by clicking a link or opening an attachment.
“A threat actor gets into your operating environment and compromises a legitimate e-mail account,” Ballesteros said. “It could be through a vendor. They’ll use that to get a foothold into a person’s network and then execute whatever type of attack you’re attempting.”
Members of the public might be surprised by some of the dollar values CISA has assigned to certain kinds of data (see graphic below).
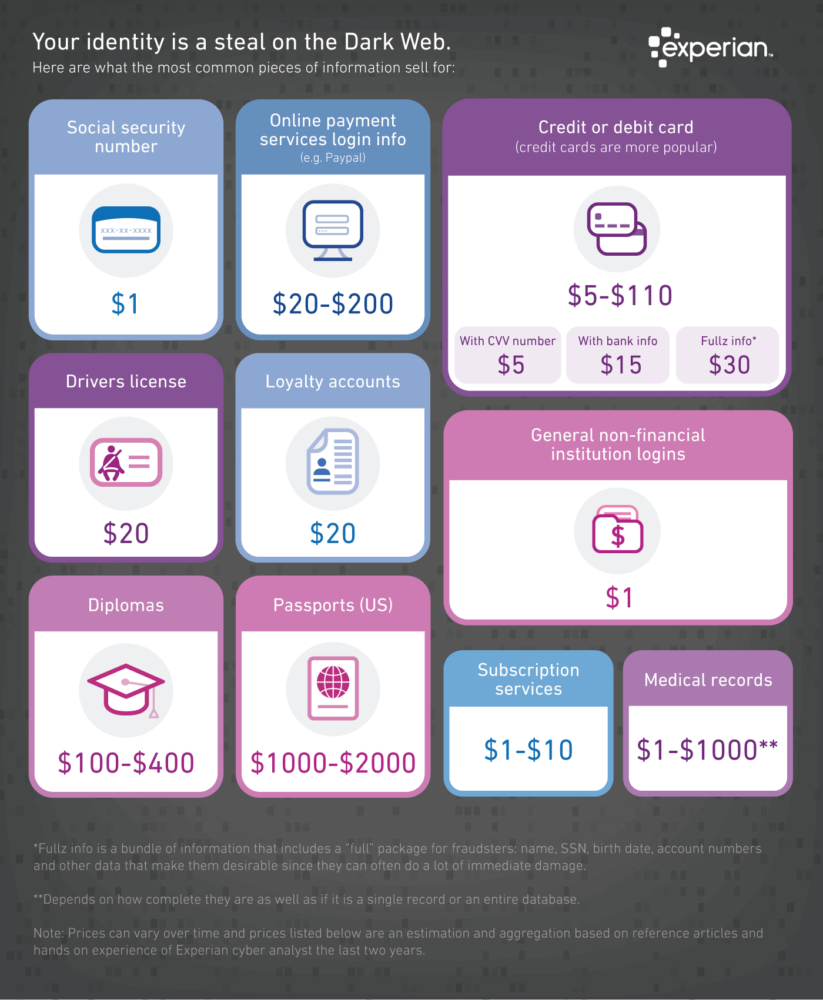
An individual’s Social Security number is only valued at $1, while a driver’s license is worth $20. By contrast, a passport is worth up to $2,000, and online services payment log-in information is worth anywhere between $20 and $2,000 depending on how deep the data goes.
To contact CISA and schedule a Risk and Vulnerability Assessment, e-mail central@cisa.dhs.gov.
For training on incident responses, go to https://www.cisa.gov/incident-response-training
For training on cybersecurity related to industrial control systems (ICS), go to https://ics-training.inl.gov/learn/signin.
United States Secret Service
While people usually associate the Secret Service with protecting the president and wearing suits and dark sunglasses, the agency actually does quite a few things for the public – particularly in the area of cybersecurity.
Agent Clarke Skoby explained that, in addition to doing conferences like NMFTA’s, he also assists with tabletop exercises and offers law enforcement the use of a large forensics lab in Houston. In addition, local offices like Houston have multiple network intrusion response agents, who will show up at your door to help if you have a vulnerability.
“The majority of the times when they respond are proactive,” Skoby said. “They might get wind of something and show up at your door and say, ‘Hey, you guys might have an issue.’”
The Secret Service is part of the Department of Homeland Security. Prior to the establishment of DHS, the Secret Service was part of the Treasury Department – and that pedigree is still reflected in its mission.
“Most of our investigations have some sort of financial nexus to them,” Skoby said. “We protect the financial infrastructure, the payment systems. We respond to ransomware investigations. We’ll show up, collect data, get information, try to figure out which variant the ransomware is.”
If you need help from the Secret Service on a cybersecurity crime, contact your local field office. A directory of these offices is here: https://www.secretservice.gov/contact/field-offices
The Secret Service will eventually turn over that information to the lead agency on ransomware investigations, which is . . .
The Federal Bureau of Investigation
Trina L. Martin is a member of the FBI’s Cyber Task Force and offered an assessment of some of the cyberthreats facing the nation and the world today.
The FBI is the lead agency for major cybercrimes such as ransomware attacks but also works to investigate more personal crimes – including those by predators who may intimidate or threaten young people into sending information or even photos.
Martin reviewed the cyberthreat landscape for 2024 and urged conference attendees to practice fundamentals like multi-factor authentication and strong passwords and to be careful about clicking links in seemingly innocent e-mails.
When any sort of federal crime is committed in cyberspace, the FBI is the lead investigating agency.
If you need to contact the FBI about a cybersecurity crime, contact your local field office using the following directory: https://www.fbi.gov/contact-us/field-offices. You can also report the incident by going to https://www.ic3.gov/complaint.
Transportation Security Administration
While many people may associate the Transportation Security Administration with airport checkpoints, the TSA in fact works very closely with other federal agencies to root out threats to all transportation modes – especially when it comes to cybersecurity.
TSA assists with cybersecurity assessments and training, with particular emphasis on the role of people and security awareness. TSA also helps companies work through a Cybersecurity Evaluation Tool that helps the companies get ready for new regulations that might be coming out.
“And they’re coming quickly,” said Takeda Parker-Bradford, TSA compliance administrator.
Coming regulations, Parker-Bradford said, focus on ensuring transport companies make full use of access controls so they don’t compromise their environments.
“We want to ensure your environment is not being modified without your knowledge,” she said.
A top TSA priority right now is helping transportation companies that are still using older technology protect themselves against attacks.
“One of our focuses is dealing with some of the legacy equipment that is still heavily in use, and can’t get the same updates or patching,” Parker-Bradford said. “How do we combat something that has not yet come to life? With ransomware being such a prevalent attack vector, there has been difficulty getting information on attacks as they are occurring.”
To learn more from TSA about cyber incident responses, go to www.dhs.gov/cyber-incident-response.
To report a cyber incident to TSA, e-mail info@us-cert.gov.
For information from the National Cybersecurity and Communications Integration Center, go to www.dhs.gov/national-cybersecurity-and-communications-integration-center.
TSA also has a Transportation System Sector Cyber Working Group. To be invited to participate, e-mail cybersecurity@tsa.dhs.gov.
When it comes to cybersecurity, the government really is here to help. And because the trucking industry has been designated part of the nation’s critical infrastructure, these resources are widely accessible to carriers and those who support them.
Take advantage of these resources to help you be better protected and prepared. The stakes have never been higher.
To view photos from the conference, access our event photo album.







